How to verify integrity of a file using SHA256
Did you download an application from internet and not sure whether it is legitimate or modded? Checking the digital signature of an application can be useful in these case where you want to know about the integrity of the softwares. Most commercial softwares or applications do not provide the MD5 or SHA-X checksum, but most open-source or free programs do. Here is a quick guide how to verify an application software using SHA-256.
Requirements:
- shasum CLI tool (for linux and MacOS only).
- Familiarity with command line interface.
Step 1
Check whether shasum CLI tool is installed in your system. Open terminal or any other shell and write the following command to check whether shasum CLI tool is installed in your system or not. If it shows the path, then you are good to go, otherwise you need to install the shasum CLI using your favorite package manager (Apt for ubuntu, Homebrew for MacOS)
which shasum
Step 2
Run shasum tool with appropriate SHA algorithm. For instance, we are testing MacTeX tool for this purpose. http://www.tug.org/mactex/mactex-download.html. Fortunately, the website provides SHA256 along with SHA512 and MD5.

shasum -a 256 /Users/smshovan/Desktop/MacTeX.pkg
The last portion of the command is the file location, in our case, we placed MacTeX.pkg in the Desktop folder.
The tool may take some time (it took me around 22 seconds) depending on the system and application size.
Step 3
Match the generated checksum and the provided checksum of the official site. If it matches, the application is legitimate or vice versa. In our case, it matches. So we are safe to install the application what we downloaded.
- To know further about shasum tool, use the following command to see the manual of the shasum.
man shasum

Let's compare a crack (Reverse Engineered) and legitimate applications. Texpad is a modern software for writing latex code. It cost around 30 bucks. Let's compare the checksum generated by the two softwares.
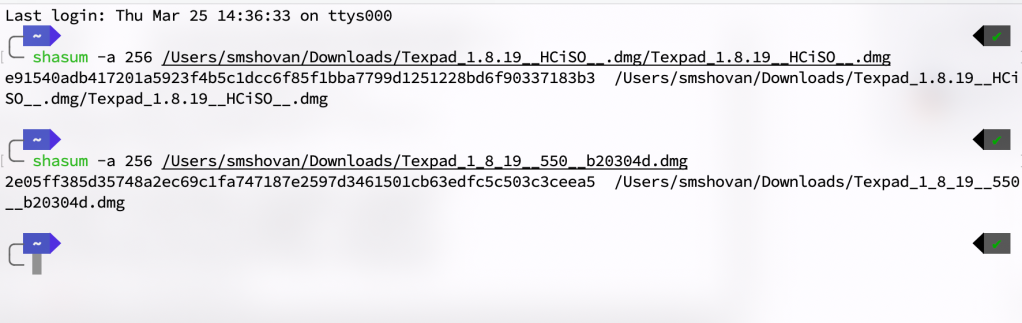
The checksums are completely different to each other !!!
People download crack version for free and they think the software is harmless. But here we will see, two softwares are not exactly same. Crackers can intentionally write codes hidden to another reputed software that can be a threat to privacy and security. Don't take for granted as softwares to be free. If you cannot afford, you should look forward to free alternatives, or save your pocket money to buy the tool you need in your life rather than risking your valuable information to be compromised.
Comments
Post a Comment